Concerns regarding climate change, together with the economic opportunities of green energy, are driving the adoption of renewable distributed energy resources (DERs). Yet, due to their distributed nature and multiple involved parties, DER sites can present a large cyberattack surface amid a fast-evolving threat landscape, creating major access management security challenges.
Today, too many DER sites rely on security models that slow innovation and are vulnerable to compromise. As energy companies become a top target for ransomware and other cyberattacks, change is needed.
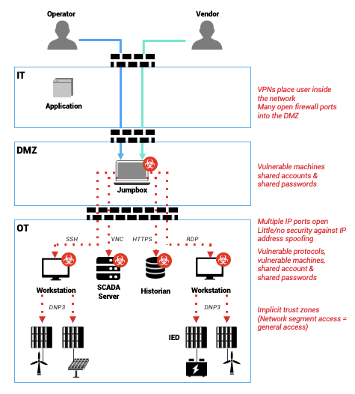
Traditionally, power producers use perimeter-based and zone/layer-based models to design a security architecture for asset protection. Meanwhile, North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) regulations and International Electrotechnical Commission (IEC) 62443 guidelines significantly restrict the number of technicians allowed to access these assets, as all participants are required to meet standards with specific training and background checks to access, operate, and maintain sites. Existing approaches seek to control access to Operational Technology (OT) systems using a complex network architecture that includes numerous firewall rules, jump servers, password vaults, authentication software, Virtual Private Network (VPN) connections, poorly secured machine and desktop access protocols, and multiple interfaces and scripts for managing user access.
This approach can prove vulnerable and costly. As the number of DER sites and participants continues to grow, so does the risk of a significant disruption in power supply. Simply using the same perimeter-based tools and techniques for DERs as were previously in use at single-party large generation locations will become problematic. More parties will require access to significantly more sites as the generation mix evolves. Even though individual DER sites may be smaller and subject to fewer cybersecurity regulations than traditional energy generation facilities, access should still be controlled based on a person’s identity, role, and training as described in many cybersecurity guidelines, including NERC CIP, IEC 62443, and the National Institute of Standards and Technology (NIST) Cybersecurity Framework, to prevent distributed power generation falling victim to a distributed cyberattack.
Independent power producers’ IT and operational organizations spend a significant amount of time and money on not only network and security design and implementation, but also ongoing maintenance to keep security controls updated and patched for protection and compliance needs. And, of course, unguarded open firewall ports, stale, or shared accounts on jump boxes and workstations, VPN-enabled network access, and poorly terminated access-protocols like remote desktop protocol (RDP) and virtual network computing (VNC) all provide entry-points for hackers if not secured.
Using this traditional approach, secure remote access for DERs is both expensive and inefficient; and more importantly, it becomes even more vulnerable to cyberattacks over time.
The Challenge with Multi-Party Access
The frequency of DER workforce changes across multiple parties only exacerbates these issues. Owners, operators, asset managers, vendors, and manufacturers all require differing levels of on-site and remote access over the generation asset’s lifetime. Independent power producers and operators of the assets will need to ensure security compliance that include secure access. Asset management and industrial manufacturers or vendors must ensure all financial and contractual requirements are met, which often include service level agreements or requirements directly attributed to regulatory compliance needs of owners and operators.
With traditional security strategies, operators responsible for controlling remote access must grant broad access and simply trust that users will only access specific sites or specific onsite devices—essentially creating an honor system to avoid enacting complex, overlapping network policies that complicate access altogether.
Using today’s typical tools, operations would be required to set up several different products and configurations to provide multi-party remote access to a single site. Listed below are just some of the typical products to license, configure, and maintain for remote access:
:
- VPN software for network authentication and access
- Identity access management software for authentication and optional features, i.e., multi-factor authentication (MFA), Single Sign-On
- Privileged access control and password vault
- Scripts as necessary for device password rotation
- Firewalls, associated network and port configurations, i.e., modem IP whitelisting, local (site) active directory, and domain controller set up and management
- A physical server, windows accounts to host ICS and device engineering software
- File transfer servers and malware scanners to move files (programs, data, etc..) in and out of the DER environments.
These efforts are not trivial for a single site, and the nature of distributed generation is to have many sites under management that require the same level of protection. This makes today’s tools and techniques unscalable for the power industry transformation.
| Entity | Responsibility | Access Needs |
|---|---|---|
| Asset Owner | If NERC registered facility must comply with all applicable NERC Generator Owner requirements. | Will vary, may want remote access for reporting verification, asset management, etc |
| Vendors | Numerous supply equipment and service providers are needed to support the facility. Typical providers will include an inverter, HV substation, data management, SCADA integrator, and compliance program providers. | Will require full remote and, at times, local access for maintenance and troubleshooting of equipment. Service providers will need access to operational data for compliance reporting. Access may be scheduled, ad hoc, or conditional. |
| Asset Manager | Responsible for all financial and contractual requirements for the various sites. Represents the asset owner ensuring all parties and operators meet all contractual obligations and may include the Generation Operator is compliant. | Requires limited remote access and depends on the contractual involvement with the scope of supply with the asset owner. |
| Operators | Responsible for the operation of the site and must meet all NERC Generation Operator compliance regulations. | Requires full remote and local access throughout the commissioning and operation of the site. |
The Impact of Zero Trust & End-to-End Orchestration
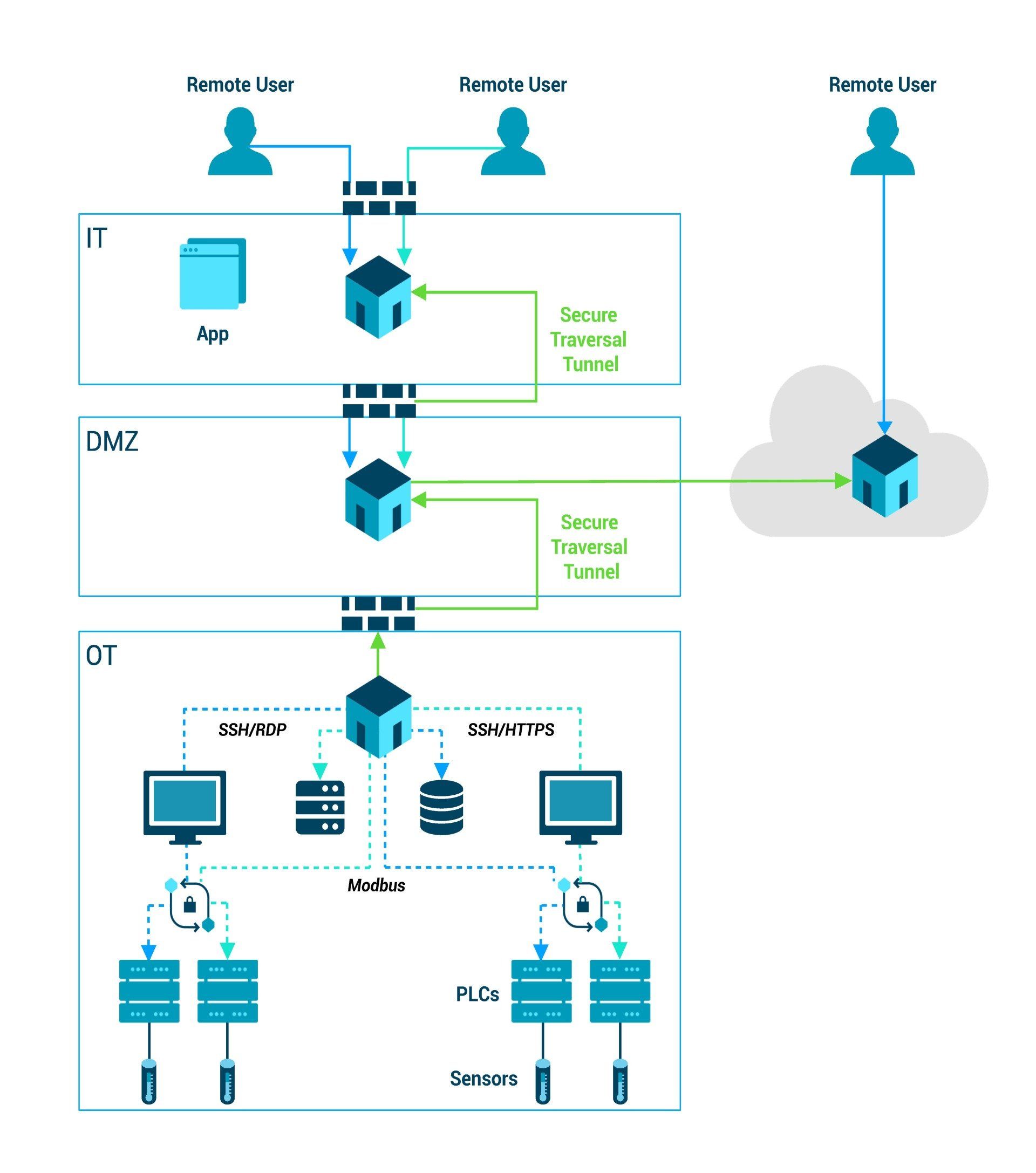
Fortunately, the challenges of multi-party access can be managed with zero trust. Solutions like Xage Fabric enable end-to-end orchestration along with centralized policy management and distributed policy enforcement. This makes multi-party access simple to use, administer, and audit while minimizing the attack surface of remote DER operations.
A major principle of zero-trust is for security policies to define what can be done
by, and done to, each individual identity. For DERs, identities serve as the core security idea - a user’s identity defines the extent to which a user can traverse from outside the enterprise to the DMZ to the operation, while a device’s identity determines, at the level of the individual device, which users and applications are permitted access. To enjoy the benefits of this granular access management, DERs need an access control solution that embodies the zero-trust principles set forth in NIST SP 800-207, including:
- Individual access perimeter based on an identity of each user and an asset, not just party, site, or network segment
- Distributed enforcement of access policies with the ability to automate and orchestrate across typical IT, DMZ, and OT network boundaries
- Centralized policy management built around identities of people, applications, workstations accounts, and devices that also supports multi-party access
- End-to-end orchestrated access control based on authenticated user identities
- Ability to orchestrate necessary protocol breaks between zones for compliance
With Xage Fabric’s zero trust remote access solution, independent power producers and operators can reduce costs for not only their power and IT operations but also for vendors and suppliers.
| Key Benefits & Cost Avoidance | Xage Fabric Capability |
|---|---|
| IT costs and VPN software and associated licensing, maintenance and configuration costs for all users needing access. | Once the user’s identity is authenticated, the Xage Fabric proxies a remote session in the remote user’s browser for only the assets allowed by policy for that user’s identity. |
| Eliminate malware threat of uncontrolled third-party computer. | Machines authenticated to the Xage Fabric are never granted access inside the network and network IP addresses are not exposed to the remote machine. For file transfer operations, the Xage Fabric supports encrypted and signed transfers, with multiple malware-scanning options. |
| IT management of firewall port, VPN, Sublan, ACL, and server accounts including coordination with third parties for access. | The Xage Fabric automates many network security functions and provides orchestrated, multi-hop access for just-in-time access. The Xage Fabric creates and terminates encrypted IPSec tunnels between Fabric Nodes with necessary protocol breaks for end-to-end access spanning network segments. Windows accounts are created dynamically for each user session and disabled after the session is terminated. The Xage Fabric requires a single firewall rule no matter the number of access methods or application protocols required by the facility and requires both ends of the tunnel to be properly signed to prevent spoofing. |
| Visibility and control of third-party interactions to DER assets. | Power Producers can control third party remote access for individual devices (smart inverter, etc) or engineering workstation level based on several access policies including ad hoc requests, specific timeframes, and physical location of assets. Every interaction is logged and includes a session recording of the interaction. |
By adopting a solution that can manage identities and access policies in a multi-party environment—using zero-trust principles of “just-in-time” and “just-enough-access” coupled with orchestrated and granular access controls securing interactions to individual assets—power producers can operate and collaborate across many distributed sites with a significant reduction in risk at a much lower cost.
Further, the effects of this security architecture will do more than thwart off cyber threats. Eliminating the attack vectors of shared accounts, VPN connections and open firewall rules will reduce IT, operational, and capital expenses. And as demand for renewable energy continues to climb, the connectivity derived from such granular access controls will offer an essential foundation for innovation and growth.